Make Rainbow Tables Great Again
About
A Case for Modern Rainbow Table Usage
Rainbow tables went out of style a few years ago when GPU-accelerated password cracking became popular. With tools like hashcat, it no longer made sense to invest the effort to obtain the existing obsolete tables. Furthermore, no GPU-accelerated open-source tools existed to create new tables with. For these reasons, the world of rainbow tables was forgotten by the infosec community.
However, rule-based cracking and rainbow table cracking were never exclusive strategies. They were (and still are, in fact), complementary. Rules are great at finding patterns, which are commonly set by users; rainbow tables are effective against fully random passwords, which can exist for highly sensitive accounts.
For example, if the database of NTLM password hashes for a Windows domain were obtained, the optimal strategy would be:
- Use hashcat to brute-force all 1-7 character passwords (this can be done quickly).
- Use hashcat to crack passwords based on rules (variable time).
- Use rainbow tables to break complex 8-character passwords (a few hours).
- Use rainbow tables to break complex 9-character passwords (a few days).
While brute-forcing 8-character passwords is very much possible with hashcat, it is inefficient to do so for smaller numbers of hashes:
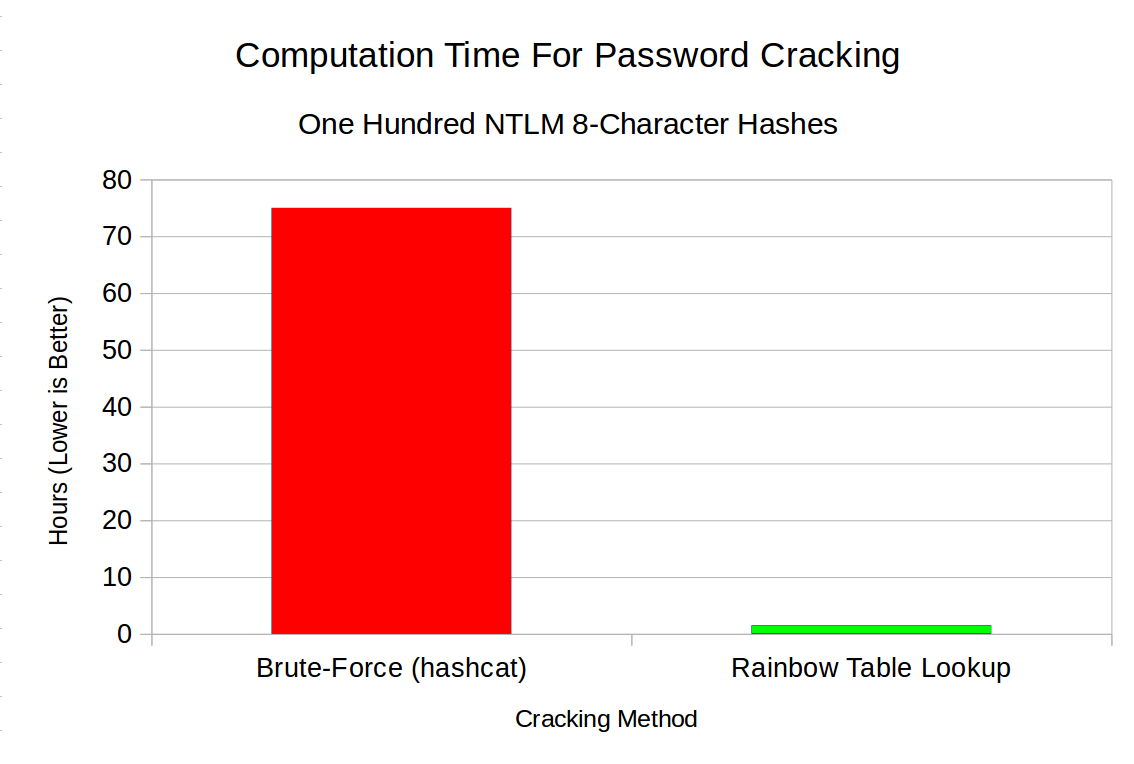
Hashcat arguments used: "-m 1000 -a 3 -w 3 -O hashes.txt ?a?a?a?a?a?a?a?a"
As shown in the graph above, on a machine with a single NVIDIA RTX 2070 GPU, hashcat takes roughly 75 hours to brute-force one hundred 8-character NTLM passwords, whereas the Rainbow Crackalack software (with the NTLM-8 tables) achieves a 93% success rate in an hour and a half!
The following graph shows the cracking times for 9-character NTLM hashes:
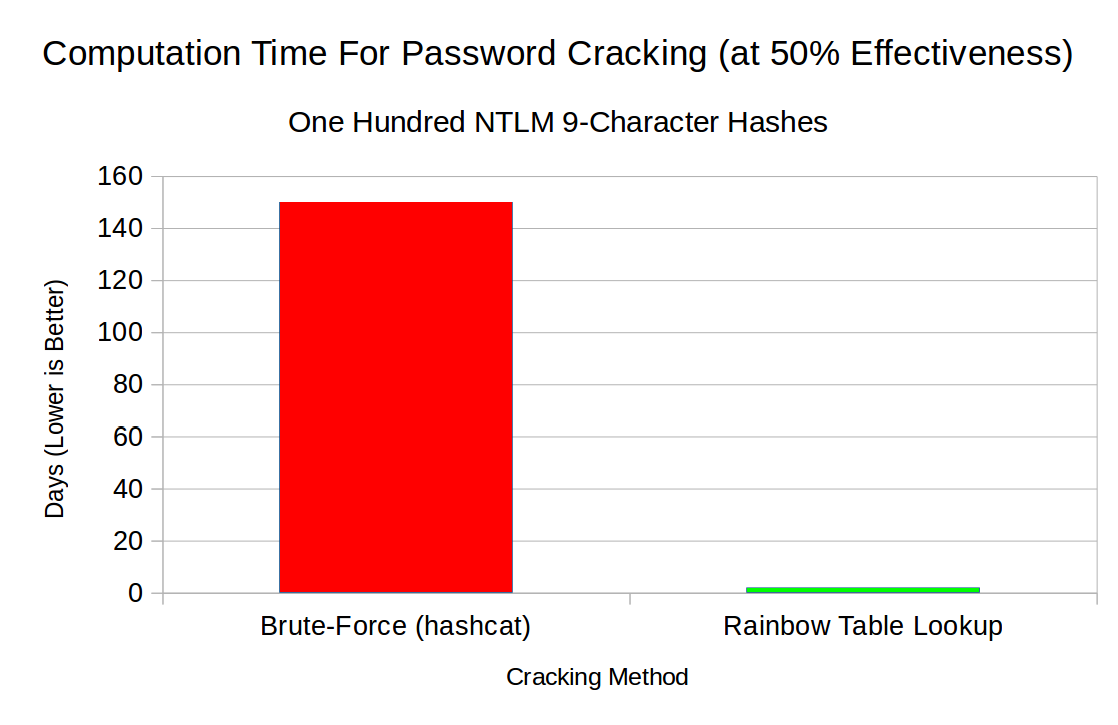
Hashcat arguments used: "-m 1000 -a 3 -w 3 -O hashes.txt ?a?a?a?a?a?a?a?a?a"
The graph above shows that, on a machine with a single NVIDIA RTX 2070 GPU, hashcat would take an estimated 150 days to crack 50% of 9-character NTLM hashes, whereas rainbow tables would do it in a little over 2 days! (51 hours, to be exact)
Cracking Example
The following example shows one hundred NTLM 8-character password hashes being cracked by the crackalack_lookup tool:
News
February 26, 2021Version 1.3 was released, which includes massive speedups for NTLM 9-character lookups. Precomputation times are 9.5x faster, and false alarm checks are 4.5x faster!
April 2, 2020The NTLM 9-character tables are now available! Furthermore, version 1.2 of the software was also released, which features a 30-40% speedup on lookups due to parallel table loading. The full announcement can be found here.
August 8, 2019Version 1.1 was released today. It features massive speed improvements (credit Steve Thomas), finalization of the NTLM9 spec, and various improvements and bugfixes.
June 11, 2019Today marks the launch of the project! The source code for table generation and lookup is now available, along with tables targeting NTLM 8-character passwords. Our Kickstarter project aims to raise funds for more equipment so we can generate NTLM 9-character tables!
Volunteers
Although the original Kickstarter project failed to reach its funding goal, volunteers from around the world nevertheless stepped up and generated 10 terabytes of raw 9-character tables over the course of 8 months! A round of applause for their dedicated work!:
- John Alves
- An Anonymous Contributor
- Clement Billac
- Joffrey Czarny (aka Sn0rkY)
- Y. Dimitrov
- Patrick Eisoldt
- Jamie Gillespie
- Aaron Jones
- Liu Ke
- Marco Nesler
- Abdurrahman Bahadır Temizer
- Joe Testa
- Sandro "guly" Zaccarini
Download
The source code for table generation and lookup is available on Github. Pre-compiled executables for Windows are available as well.
NTLM 8-character tables can be downloaded for free via BitTorrent. These are 93% effective and are 486 GB in size.
NTLM 9-character tables can also be downloaded for free via BitTorrent. These are 50% effective and are 6.7 TB in size.
Contact
You may contact us using this form or by reaching out to @therealjoetesta on Twitter.
